DORA: the countdown has begun
Next year, more than 3,600 companies in Germany must implement theEU Regulation DORA. The regulation is intended to better protect the financial sector against cyber threats. What is the exact timetable? And what awaits companies of the financial sector? From Jens Obermöller, Director General – IT Supervision
In summer 2023, the cyber gang Clop exploited weaknesses in the data transfer programme MoveIT. Around the world, thousands of companies and their customers were affected by data leaks. These included a large number of German financial institutions and insurance undertakings working with third-party service providers that use this programme.
The example illustrates how greatly dependencies in the financial sector have increased. The failure of internal IT systems or cyberattacks can have severe consequences that reach far beyond the companies directly affected by this. Such disruptions pose risks even if they do not occur at the financial institutions themselves. The importance of critical third-party service providers is therefore on the rise. Their role is to manage key tasks for a large circle of companies of the financial sector, which leads to high concentration risks.
Cyber threats in BaFin’s focus
BaFin has been focussing on these threats for a long time – and has placed corresponding demands on the IT of banks, insurers, asset management companies and payment service providers . At the European level, the Digital Operational Resilience Act (DORA) has now set out standardised requirements for managing cyber threats and ICT (information and communication technology) security in the financial sector.
DORA’s most important accomplishment is the creation of a single rulebook, i.e. a regulatory framework for managing ICT risks that is applicable throughout Europe. Estimates show that DORA applies to more than 20,000 financial entities in Europe. Practically all institutions and undertakings already supervised as well as numerous other third-party service providers are obliged to adhere to this regulatory framework. In Germany, DORA is applicable to over 3,600 entities of the financial sector.
Timetable until application
The EU regulation came into force in January 2023, and institutions and undertakings will have to comply with the DORA requirements from January 2025 (see Figure 1). The three European Supervisory Authorities – the European Banking Authority (EBA), the European Securities and Markets Authority (ESMA) and the European Insurance and Occupational Pensions Authority (EIOPA) – have been jointly developing regulatory technical standards, implementing technical standards and guidelines intended to further specify DORA.
Figure 1: DORA – development and further timetable
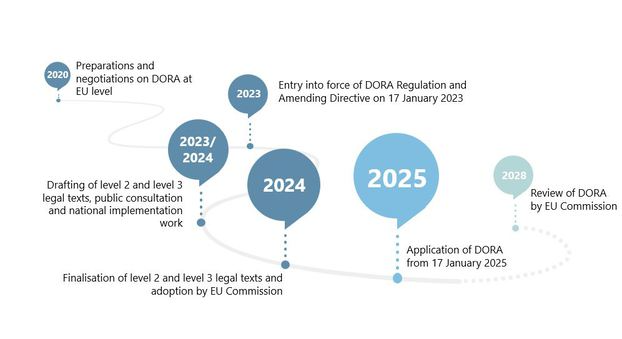
Source: BaFin
ICT risk management: responsibility cannot be delegated
A core element of DORA are the requirements for ICT risk management (see Figure 2). These are aimed at strengthening companies’ resilience against cyber threats and enabling them to keep their processes running, even during or after a disruption. The regulation stresses that the responsibility for managing a company’s ICT risks lies at management level, i.e. with the managing directors or members of the executive board.
And not only that – the responsibility for defining and approving a strategy for digital operational resilience and appropriately budgeting the costs also lies with them. The necessary expertise must be up-to-date at all times. The companies of the financial sector are additionally obliged to establish an ICT risk control function. This contains elements of the information security officer function already set out in the supervisory requirements for IT, but differs in other respects.
To counter ICT risks, it is imperative that the ICT risks are managed thoroughly and comprehensively and that the measures are well-documented. The concrete requirements for this are geared to international, domestic and sector-specific best practices and standards. In terms of standards and technology, DORA is essentially neutral – it is designed to enable the companies of the financial sector to implement the requirements according to a risk-based and proportional approach.
Figure 2: Art. 5 Governance & Organisation
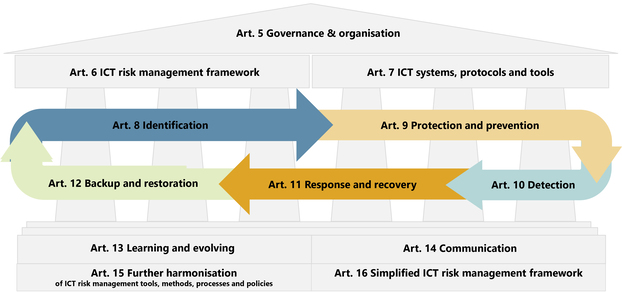
Source: BaFin
Requirements for reporting ICT incidents for the entire financial sector
DORA requires companies of the financial sector to manage ICT-related incidents with due care and attention. Financial entities must monitor, log and report all ICT-related incidents and base their classifications on the criteria set out in Article 18 of DORA. Major incidents must be reported to the competent supervisory authority.
For many supervised companies, this is nothing new – payment service providers are currently obliged under the Second Directive on Payment Services (PSD II Directive) to observe similar reporting and notification requirements. The EU Directive on measures for a high common level of cybersecurity across the Union (NIS 2 Directive) also sets out such specifications for critical infrastructures within the meaning of the German Act on the Federal Office for Information Security (Gesetz über das Bundesamt für Sicherheit in der Informationstechnik – BSI Act).
DORA standardises these obligations, extends them to include the entire financial sector and names BaFin as the recipient of these reports. BaFin promptly passes the reports on to the BSI, the respective European supervisory authority (EBA, ESMA or EIOPA) and, if applicable, other parties involved, such as the European Central Bank. Besides the reporting system for ICT-related incidents, DORA is also introducing a voluntary system for reporting significant cyber threats.
Financial entities must test digital operational resilience
Under DORA, all financial entities are obliged to thoroughly review their information and communication technology by establishing a risk-based, proportionate testing programme. Exemptions with regard to the testing programme, but not the testing obligation, are in place for microenterprises and some other financial entities under Article 16 of DORA. This testing programme is supposed, for example, to analyse open source software, assess network security and review physical security at financial entities. Other examples are scenario-based testing, compatibility testing and penetration testing.
Selected critical entities of the financial sector are additionally supposed to conduct threat led penetration tests (TLPT), which involve hackers being allocated the task of identifying IT vulnerabilities at companies. The objective is to close any security gaps. The details of these tests will be set out in the regulatory technical standards (RTS) that will draw heavily on the European TIBER-EU framework. The previous German equivalent, TIBER-DE, which was voluntary, becomes obligatory through DORA. The supervisors will provide the financial entities with an attestation confirming that a TLPT was successfully performed in line with supervisory requirements. DORA provides for cross-border recognition of these attestations. But from BaFin’s perspective, the TLPTs not only serve supervisory purposes; most importantly, they serve as a source of insight to the financial entities.
Focus on third parties
DORA also focuses on the risks that can arise when companies of the financial market use services rendered by ICT third-party service providers. Companies using these services are obliged to monitor these risks – over the entire life cycle.
A risk analysis must already be carried out before any contracts are signed. In addition, the companies are obliged to conduct a due diligence to assess the suitability of the service provider. Financial entities must consider, for instance, the extent to which they are dependent on the particular ICT third-party service provider and the risks that could arise from the contractual relationship. They require an exit strategy for critical or important outsourced functions. DORA also lays down requirements for the contractual arrangements – for example, the service provider must agree to provide support if ICT-related incidents occur that concern their services.
All ICT contractual arrangements must be documented in an information register that BaFin can use as a basis for identifying critical ICT third-party service providers. The register thus makes an essential contribution to the European oversight framework for critical ICT third-party service providers.
When should financial entities suspend the use of services rendered by a service provider?
The focus of this entirely new element of EU financial market regulation lies on ICT third-party service providers designated as critical by European supervisory authorities. An operational disruption at such service providers could heavily impact the stability, continuity or quality of financial services on the overall market. For the designation, account is also taken of the extent to which critical or important functions of financial entities are dependent on ICT third-party service providers. The costs resulting from the oversight tasks are to be funded from fees levied on critical ICT third-party service providers.
The lead overseer is ascribed a key role in this context. This function is always performed by one of the three European supervisory authorities – EBA, ESMA or EIOPA – depending on the particular sector in which the ICT third-party service provider is primarily operating. The lead overseer is supported by a joint examination team consisting of experts from national and European supervisory authorities.
The lead overseer is given rights to request information from and carry out controls and inspections at the critical ICT third-party service providers and may also impose fines. For example, it monitors whether the ICT third-party service provider is complying with the requirements for ICT risk management. In the event of irregularities, the lead overseer may make recommendations to the critical ICT third-party service providers. If the service provider fails to heed these recommendations, the national supervisory authorities – including BaFin – may call upon the financial entity to temporarily suspend collaboration with the service provider or even stop cooperating with the provider entirely. Certain measures can also be published on the websites of the European supervisory authorities.
Preparing for emergencies through exercises
DORA advises financial entities to exchange amongst themselves information and intelligence about cyber threats, such as indicators of compromise. Entities are advised to also share attackers’ tactics, techniques and procedures as well as cyber security alerts and configuration settings for relevant systems so that they can learn from each other.
BaFin wants to actively participate in this exchange, too. As the future recipient of reports on ICT-related incidents, BaFin will be in possession of valuable information that will benefit the entire financial market. Crisis management and contingency exercises will also shift even more into BaFin’s focus in future. After all, both the financial entities and Germany’s supervisors will need to be prepared for emergency scenarios – in other words, cases in which all preventive measures and defence mechanisms fail to take effect. The best means for financial entities to prepare themselves for such extreme scenarios is through exercises. In this way, cross-sectoral communication channels and reactions can be tested and the collaboration in crisis situations optimised.



















































First, please LoginComment After ~